 Red bulbs aside
Red bulbs aside
2020-Dec.-11
Each Tor exit node can specify its own exit policy. This policy is a set of rules that allow or deny traffic exiting from the relay [1][2].
The question here was to study if each exit node could really honor the exit policy its annouces. The aim is to detect situations where an exit node wants to allow traffic on a port/service but this could be blocked because of misconfiguration (e.g. firewalled) or dowstream blocking (by the hoster or ISP, because of its terms of service for example, or because he would have detected attacks/abuses). If we could detect this blocking, we could help admins to solve the situation and/or adapt their exit policy and so increase the Tor network health.
The scanner has been written as an experimental probe module for exitmap, a fast and modular Python-based scanner for Tor exit relays. Tests have been set up to start with the port 25 that is used for SMTP. It has the following advantages:
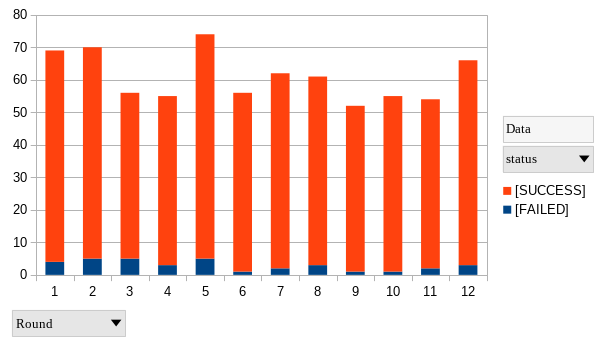
12 rounds of tests have been down in two weeks.

Results show that in an average population of 58 relays allowing exiting on port 25, 1 to 5 of them give an error on each round. The average rate of error is 4,9%. Results have been confirmed with manual tests showing the blocking of port 25 but the possibility to use the same circuit for other usages.
We then studied precisely relays raising errors during the test to compare to their global statistics.
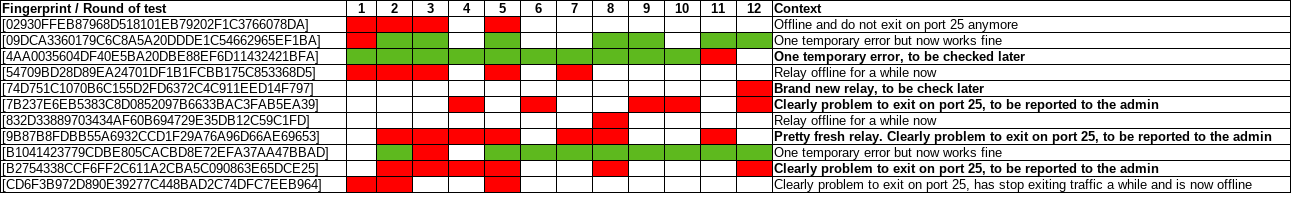
The results shows consistent analysis between the probe module and the real situation of the exit node. Five relays are listed for further actions:
The 3 relays have been reported to bad-relays@lists.torproject.org. The probe module will be pushed to the exitmap module in a few days.
The aim is to be able to assess ports/services that represent a frequent use on the network. So other probes will be developed then.
Should you have any comment on this page, get in touch !